Businesses generate petabytes of data at varying speeds and volumes every single day. With the increased use of cloud storage, the risk of security incidents also rises. A security breach could be a simple error that leaves data exposed or a malicious social engineering attack. Therefore, it is critical to have a robust data security strategy in place.
Amazon S3 security can be a cornerstone of this strategy.
Overcoming Data Security Challenges: A Strategic Approach
The responsibility for data security in a cloud environment is a shared one. AWS is responsible for protecting the infrastructure that runs Amazon S3, while you are responsible for securing your data. Security breaches caused by the misconfiguration of S3 security settings can lead to costly consequences.
- Confidential data can be held hostage by hackers for financial gain
- Sensitive information about organizations can be distributed
- A loss of clients, reputation, and revenue
Protecting your data should be a top priority, and we can guide you through the most effective techniques for securing it on Amazon S3.
Are you struggling with data security in the cloud? Learn how we’ve solved the Top 4 AWS Data Security Challenges to help you protect sensitive information, ensure compliance, and secure your cloud environment.
5 Best Practices for Amazon S3 Security You Need to Implement Today
You can use several features on Amazon S3 to bolster the security of your data depending on your business requirements. Follow these five best practices to secure S3 buckets and make sure your data stays protected.
1. Apply S3 Block Public Access Settings
By default, new buckets and access points restrict public access over the internet. However, bucket policies, access point policies, or object permissions can be modified to allow public access. A common security mistake users make is accidentally granting public access to their S3 storage. That means any sensitive data stored can potentially be accessed by anyone via a URL.
S3 Block Public Access is a simple feature that applies blanket protection against accidental public access. You can set up centralized controls to restrict access to your Amazon S3 resources. S3 Block Public Access settings override any policies and permissions to limit public access to your buckets.
We highly suggest enabling the S3 Block Public Access feature at the account level, which ensures all your existing and future S3 buckets will be automatically protected from public access.
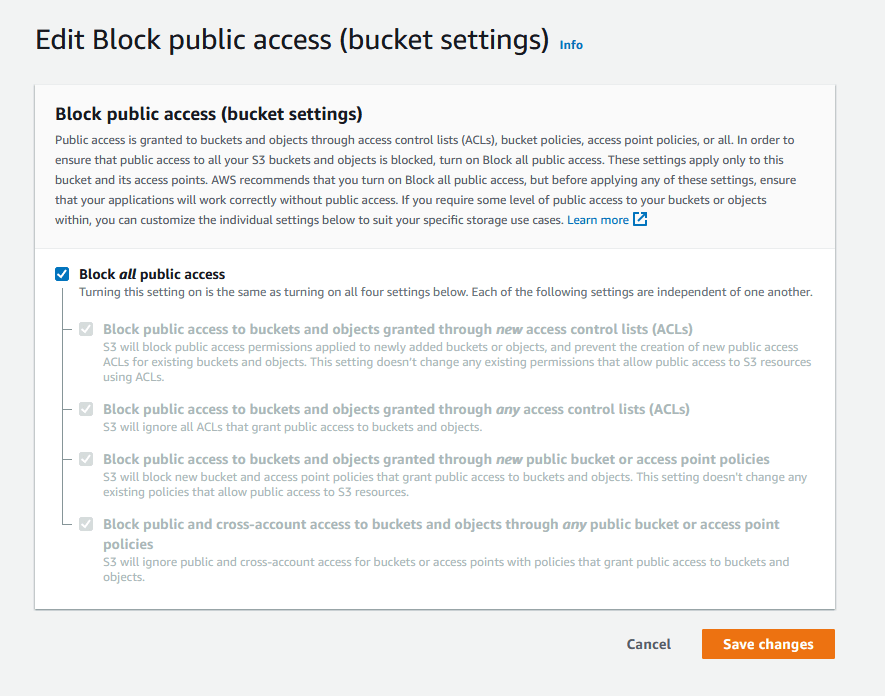
Important Updates on S3 Public Block Settings:
As of April 2023, Amazon S3 will change the default settings for S3 Block Public Access. For all new S3 buckets created after this update, S3 Block Public Access settings will be automatically enabled to ensure best practices are being followed for securing data.
2. Establish Least Privilege Access
Amazon S3 buckets allow you to configure fine-tuned access controls. Most users and applications only require a small subset of access permissions to complete their tasks. Establishing least privilege access is vital in mitigating the security risk and impact caused by mistakes or malicious intent. Therefore, you should grant the bare minimum permissions required to perform a task.
To implement least privilege access, you can utilize the following resources:
- Amazon S3 Actions and Permissions Boundaries for IAM Entities
- Bucket policies and user policies
- Service Control Policies (SCPs)
- Amazon S3 Access Points for shared buckets
Latest Innovations with S3 Bucket Access:
Amazon S3 Access Points simplify data access for any AWS service or application that stores data in shared buckets. A new update by AWS enables bucket owners to authorize access via access points created in other AWS accounts. This allows you to securely and easily share datasets with thousands of applications and users at no additional cost.
3. Encrypt Your Data in S3 Buckets
It is always a good idea to assume your data can be exposed. Keeping this in mind, you should encrypt data in S3 buckets to prevent any misuse in case of inappropriate access. AWS offers the following data encryption strategies.
Encryption of Data at Rest
You have two approaches for protecting data at rest in Amazon S3.
Server-Side Encryption: S3 encrypts your data at the object level as it writes it to disks in AWS data centers and then decrypts it when you download the objects.
Amazon S3 offers these encryption key options:
- Server-side encryption with Amazon S3‐managed keys (SSE-S3).
- Server-side encryption with KMS key stored in AWS Key Management Service (SSE-KMS).
- Server-side encryption with customer-provided keys (SSE-C).
AWS suggests turning on Amazon S3 Bucket Keys which is designed to improve performance for high-volume workloads and reduce request costs for KMS-backed server-side encryption by 99%.
Client-Side Encryption: This is more difficult to implement but is a better choice than server-side encryption. Client-side encryption requires you to encrypt the data before sending it to AWS and decrypt it after extracting it from AWS. You are solely responsible for managing the encryption process and S3 encryption keys for buckets, not AWS.
Encryption of Data in Transit
We recommend utilizing HTTPS (TLS) to prevent network traffic spying and manipulation. You should only permit encrypted connections via the AWS: SecureTransport condition on Amazon S3 bucket policies. Additionally, use the s3-bucket-ssl-requests-only managed AWS Config rule for continuous monitoring purposes.
Latest Innovations with S3 Bucket Encryption:
Amazon S3 now applies server-side encryption with Amazon S3-managed keys (SSE-S3) as the default level of encryption for S3 buckets. All new object uploads to Amazon S3 are automatically encrypted with no impact on performance and without any extra charges.
4. Disable Access Control Lists (ACLs)
There are multiple ways to grant access to your data in S3 buckets, including IAM policies, bucket policies, and Access Control Lists (ACLs). ACLs predate IAM and are the original way S3 granted access to your buckets and objects. When a request is received against a resource, Amazon S3 checks the corresponding ACL to verify that the requester has the necessary access rights.
We advise using S3 Object Ownership to disable ACLs for your buckets and all objects within them. This way you take ownership of every object in your bucket and simplify access management for the stored data. S3 Object Ownership is a better method than managing individual ACLs especially when you have many objects in the bucket.
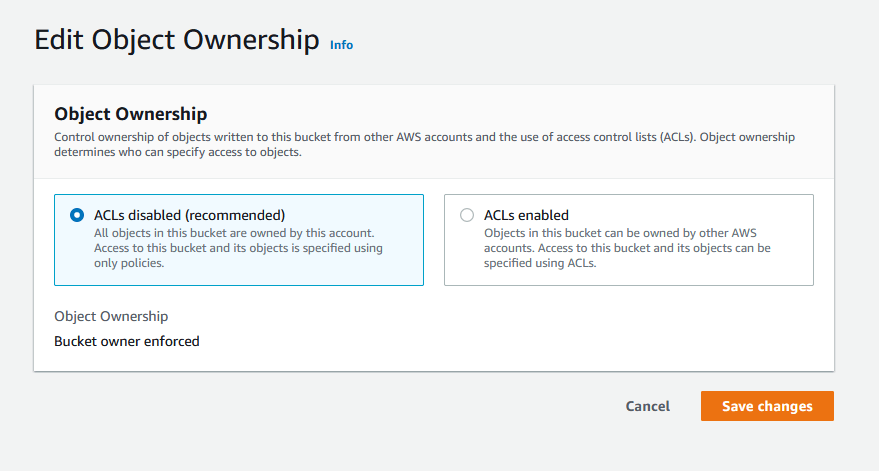
Important Updates on ACLs:
For all new S3 buckets created after April 2023, AWS will change the default settings for S3 Object Ownership. S3 ACLs will be automatically disabled after this update to ensure that security best practices are followed.
5. Enable Logging and Monitoring for Amazon S3
Logging and monitoring your S3 storage usage can help to identify any security gaps and prevent data breaches. You can leverage the following tools to gain visibility in your storage activities and apply data protection and security best practices as needed.
- AWS CloudTrail: Use AWS CloudTrail Logs with Amazon CloudWatch to get email notifications for specific API activities in your buckets. CloudTrail tracks all activities and generates audit logs that can be filtered based on your needs.
- Server Access Logging: You can enable Amazon S3 server access logging which provides detailed records of the requests made to a bucket. These logs can help you with security and access audits.
- Access Analyzer for S3: This tool checks bucket permissions across your account with a dashboard that displays public and shared buckets, along with the level and source of access. Quickly take corrective action to restore bucket access as needed.
- Amazon S3 Storage Lens: Utilize this tool to gain organization-wide visibility into object-storage usage and activity metrics, enabling you to enhance data protection. Get contextual recommendations based on S3 metrics and implement best practices such as MFA and KMS encryption.
Modernize and secure your data with our AWS Storage Services, designed to enhance security measures, optimize performance, and streamline data management for seamless operations.
Latest Innovations in Amazon S3 Metrics:
AWS has introduced an additional 34 Amazon S3 metrics to uncover deeper cost optimization opportunities, identify data protection best practices, and improve the performance of applications. Amazon S3 Storage Lens now delivers more than 60 metrics (both free and advanced metrics) on your S3 storage usage and activities.
Unlock Unprecedented Data Protection with S3 Security and Cloudelligent
Data security is a critical concern for organizations of all sizes, particularly when protecting cloud storage resources like Amazon S3 buckets, which can be vulnerable to unauthorized access and breaches. Without the right safeguards, sensitive information may be exposed, leading to compliance issues, financial loss, and reputational damage.
As an AWS Advanced Consulting Partner, Cloudelligent offers proven expertise in designing and implementing advanced protection mechanisms tailored to secure your data stored in Amazon S3 buckets. From encryption and access controls to monitoring and compliance solutions, we help you establish a fortified storage environment that ensures safety and efficiency.
Ready to take your cloud storage security to the next level? Book a Free Assessment today to get started!