The cloud is set to disrupt the IT market by nearly $1.8 trillion by 2025, as new technologies push In today’s data-driven world, the global Big Data and analytics market has surged beyond $348 billion, with projections by Statista estimating it to reach a staggering $103 billion by 2027. This rapid growth is fueled by various facets of the Big Data industry, including data centers, cloud services, IoT devices, and predictive analysis tools. As organizations increasingly rely on these technologies, ensuring robust security—especially within platforms like AWS—has never been more critical.
Our experts have highlighted some major security challenges faced by companies, from understanding the basics of AWS security to implementing best practices. We’ll guide you through everything you need to know to protect your data in an ever-evolving digital landscape.
Ready to deepen your understanding of cloud security? Dive into our blog, Understanding
the AWS Shared Security Model and discover how to effectively manage your responsibilities in securing your AWS environment.
1. Network Access Control Lists (NACL) Misconfigurations
Challenge
Network ACLs (Access Control Lists) function as virtual firewalls at the subnet level, filtering traffic to enhance security. However, a single misconfigured rule, for example: mistakenly setting a “deny” action on a critical port can cause application failures by blocking essential communication. Additionally, leaving remote server ports exposed can create significant security vulnerabilities and may invite potential risks.
Solution
Each NACL (Network ACL) rule must be carefully crafted to keep your network secure and applications running smoothly. While detection and prevention are vital, adopting a proactive approach is essential.
- Implementing AWS Security Groups and Network ACLs can help to control traffic.
- Continuously monitor your VPC traffic for anomalies and potential security issues.
- AWS provides detailed documentation and tools like AWS Config to monitor and evaluate NACL configurations.
2. Multi-Factor Authentication (MFA) Not Enabled
Challenge
Securing user access is a critical challenge, particularly as breaches linked to weak authentication are on the rise. Nearly 80% of hacking-related breaches are associated with compromised or weak passwords. Relying solely on passwords for security is increasingly insufficient due to their susceptibility to being guessed, stolen, or phished. This underscores the importance of Multi-Factor Authentication (MFA). MFA enhances security by requiring users to provide an additional form of verification beyond just a password, thereby significantly reducing the risk of unauthorized access.
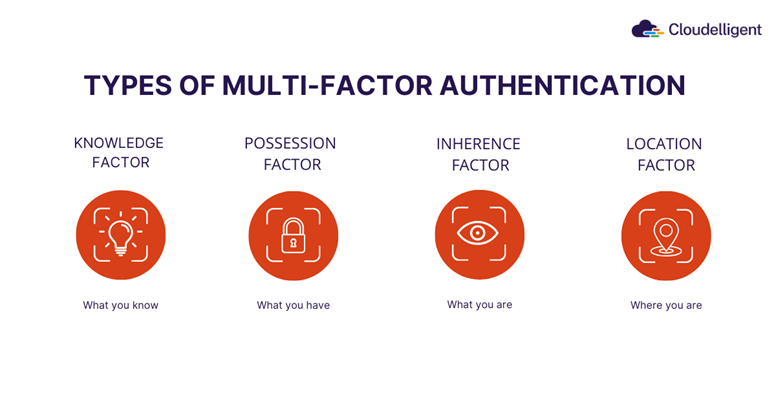
Figure 1: Types of Multi-Factor Authentication
Solution
AWS Identity and Access Management (IAM):
- Supports Multi-Factor Authentication (MFA): Enhances security by requiring an additional verification step.
- Integrates with hardware keys: Seamlessly works with devices like YubiKeys.
- Compatible with authenticator apps: Supports apps such as Google Authenticator which is an added convenience.
AWS Security Hub:
- Monitors your environment: Continuously checks for potential security risks.
- Alerts administrators: Notifies you if MFA is not enabled on critical accounts.
- Enforces security protocols: Ensures consistent application of security measures to protect sensitive data.
3. Insecure S3 Bucket Settings
Amazon S3 (Simple Storage Service) offers scalable, durable, and highly available object storage.
Widely used for storing backups, hosting static websites, serving as a data lake for analytics, and as a primary storage solution, S3 is a reliable core component of many AWS solutions.
Challenge
Unauthorized Access:
- Configuration errors in S3 buckets can expose sensitive data.
- These errors allow malicious users to access critical information.
- Addressing configuration issues is essential to maintain security.
Data Visibility & Protection Gaps:
- Insufficient oversight can lead to unforeseen risks in S3 buckets.
- Regular audits of both the contents and security controls are crucial.
- Mitigating these risks helps safeguard stored information.
Malware Upload Vulnerabilities:
- Configuration weaknesses may permit malware uploads into S3 buckets.
- These vulnerabilities present a significant threat vector.
- Timely detection and remediation are vital to protect your AWS infrastructure from cyberattacks.
Solution
- Block Public Access: Utilize AWS S3 settings, including the S3 Block Public Access feature, and prevent unauthorized access.
- Implement Least Privilege Access: Use AWS Identity and Access Management (IAM) to grant the least privileged access to S3 buckets, ensuring users only have the permissions they need.
- Enhance Data Security with Amazon Macie: Deploy Amazon Macie to improve data security visibility and enable proactive monitoring of your data security posture.
- Monitor with AWS Trusted Advisor: Use AWS Trusted Advisor to detect and alert insecure S3 bucket configurations, ensuring continuous security compliance.
If you’re looking for more in-depth information on securing S3 buckets, be sure to dive into our detailed blog, Top 5 Amazon S3 Security Strategies to Shield Your Data.
4. Challenges with Data Backup & Data Encryption
Challenge
Organizations encounter significant challenges in data management, particularly in data backup, disaster recovery, and data encryption. A major concern is the potential data loss due to accidental deletion, corruption, or ransomware attacks, which can have devastating impacts, including the loss of critical information and disruption of business operations.
Ensuring that all sensitive data is encrypted at rest and in transit is another crucial challenge. Failing to encrypt data can expose confidential information to unauthorized access and breaches, posing severe risks to security and compliance.
Solution
To address these challenges, organizations can implement several key solutions.
- Regular Data Backups: Using AWS Backup is essential to protect against data loss, therefore, allowing the restoration of data in the event of accidental deletion or corruption.
- Disaster Recovery Plans: Establish cross-region replication to ensure data can be recovered quickly and efficiently, minimizing downtime and maintaining business continuity during unexpected incidents.
- Robust Encryption: AWS Key Management Service (KMS) offers a comprehensive solution for managing encryption keys and securing sensitive data at rest and in transit, protecting against unauthorized access, and ensuring compliance with data security regulations.
Discover how Cloudelligent enhanced security for a healthcare organization using Amazon Macie. Read our blog, Amazon Macie for Healthcare Data Security to learn more.
Fortify Your AWS Cloud Security With Cloudelligent
We’ve pinpointed four key AWS security challenges that can be mitigated with specific solutions. Regular monitoring and effective use of AWS tools like AWS Shield, Amazon IAM, and AWS Config is crucial. At the same time, proper configuration and proactive management are essential. Below are the top AWS Security tools that our experts swear by.
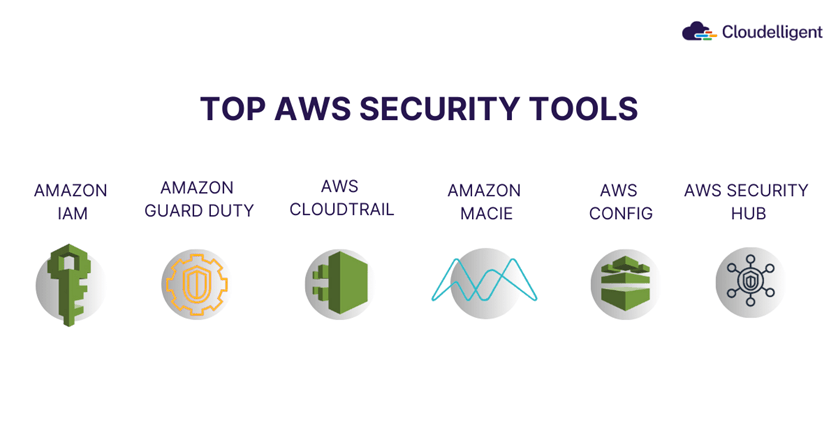
Figure 2: Top AWS Security Tools
Cloudelligent’s expert team can help you navigate these complexities, offering tailored solutions to enhance your cloud security. Contact us today to strengthen your AWS environment and safeguard your business.